Classify by Classification Rules versus Proxy Set
An important security functionality of the device is to make sure that incoming SIP dialog-initiating requests (e.g., INVITE messages) from malicious attackers are not mistakenly identified as belonging to a configured Server-type IP Group entity.
The device provides two optional mechanisms that can be employed to identify incoming dialogs as coming from a specific Server-type IP Group:
| ■ | Classification by Classification rules (Classification table): Identifies incoming dialogs based on the characteristics of the SIP message such as host part in the INVITE message (Layer 4-7) and source IP address (Layer 3). |
Recommended usage:
If the IP address of the IP Group entity is known, it's recommended to employ classification based on a Classification rule, where the rule is configured with not only the IP address, but also with SIP message characteristics to increase strictness of the classification process.
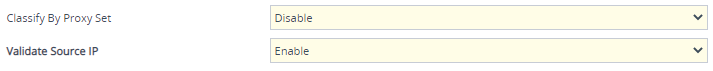
When Classification rules are used and classify by Proxy Set is disabled (see below), it's recommended to enable the 'Validate Source IP' parameter in the IP Groups table. This setting verifies that the incoming dialog was sent from one of the IP addresses (including DNS-resolved IP addresses) of the Proxy Set associated with the classified IP Group (see Validate Source IP Address of Incoming SIP Dialog Requests). IP address validation is also typically needed when multiple IP Groups are assigned to the same Proxy Set and therefore, Classification rules are necessary to produce the desired mapping (classification) of the incoming SIP dialogs to the different IP Groups.
Enabling Source IP Validation in IP Groups Table
The device uses the Classification table for classification only if the following classification stages fail (listed chronologically):
| 1. | The incoming SIP dialog is not from a SIP UA that is registered with the device (i.e., not in user registration database). |
| 2. | The Classify by Proxy Set feature is disabled for the IP Group (i.e., source IP address of incoming dialog is matched with a Proxy Set associated with the IP Group but Classify by Proxy Set is disabled for the IP Group). |
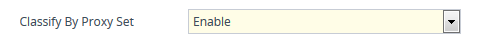
| ■ | Classification by Proxy Set: Identifies incoming dialogs based on source IP address (Layer 3) only. The Proxy Set defines the address of the IP Group. For this method, the device searches for a Proxy Set that has the same source IP address as the incoming dialog, and then classifies it to the IP Group that is assigned to this Proxy Set. Classification by Proxy Set is enabled in the IP Groups table, using the 'Classify By Proxy Set' parameter: |
Enabling Classification by Proxy Set in the IP Groups Table
Recommended usage:
If the IP address is unknown, in other words, the Proxy Set associated with the IP Group is configured with an FQDN, it's recommended to employ SIP dialog classification based on Proxy Set. This allows the SBC to classify the incoming dialog based on the DNS-resolved IP address. The reason for classifying by Proxy Set is that IP address forgery (commonly known as IP spoofing) is more difficult than malicious SIP message tampering and therefore, using a Classification rule without an IP address offers a weaker form of security.